
Learn about the new NYDFS cybersecurity regulation and the rules for basic principles of data security, documentation of security policies, and much more.
5 min read Last updated April 18, 2023
In 2017, the New York State Department of Financial Services (NYDFS) launched GDPR-like cybersecurity regulations for its massive financial industry. Unusual at the state level, this new regulation includes strict requirements for breach reporting and limiting data retention.
Like the GDPR, the New York regulation has rules for basic principles of data security, risk assessments, documentation of security policies, and designating a chief information security officer (CISO) to be responsible for the program.
Unlike the GDPR, the regulation has very specific data security control, including annual pen testing and vulnerability scans!
The point of these rules, as with the GDPR, is to protect sensitive nonpublic information, which is essentially consumer personally identifiable information or PII that can used use to identify an individual.
The NYDFS Cybersecurity Regulation (23 NYCRR 500) is “designed to promote the protection of customer information as well as the information technology systems of regulated entities”. This regulation requires each company to conduct a risk assessment and then implement a program with security controls for detecting and responding to cyber events.

The NYDFS has supervisory power over banks, insurance companies, and other financial service companies. More specifically, they supervise the following covered entities:
In short: any institution that needs a license from the NYDFS is covered by this regulation. A more extensive list can be found here.
There are some exemptions for companies that fall under the following categories:
The NYDFS Cybersecurity Regulation works by enforcing what are really common sense IT security practices. Financial companies in New York that are already rely on existing standards, say PCI DSS or SANS CSC 20, should have little problem meeting the New York regulation.
In short, NYDFS is asking organization to assess their security risks, and then develop policies for data governance, classification, access controls, system monitoring, and incident response and recovery. The regulation calls for companies to implement, at a minimum, specific controls in these areas (see the next section) that are typically part of compliance standards.
The big difference of course is that New York State regulators at the Depart of Financial Services are enforcing these rules, and that not complying with the regulation becomes a legal matter. They are even requiring covered entities to designate a CISO who will annually sign off on the organization’s compliance.
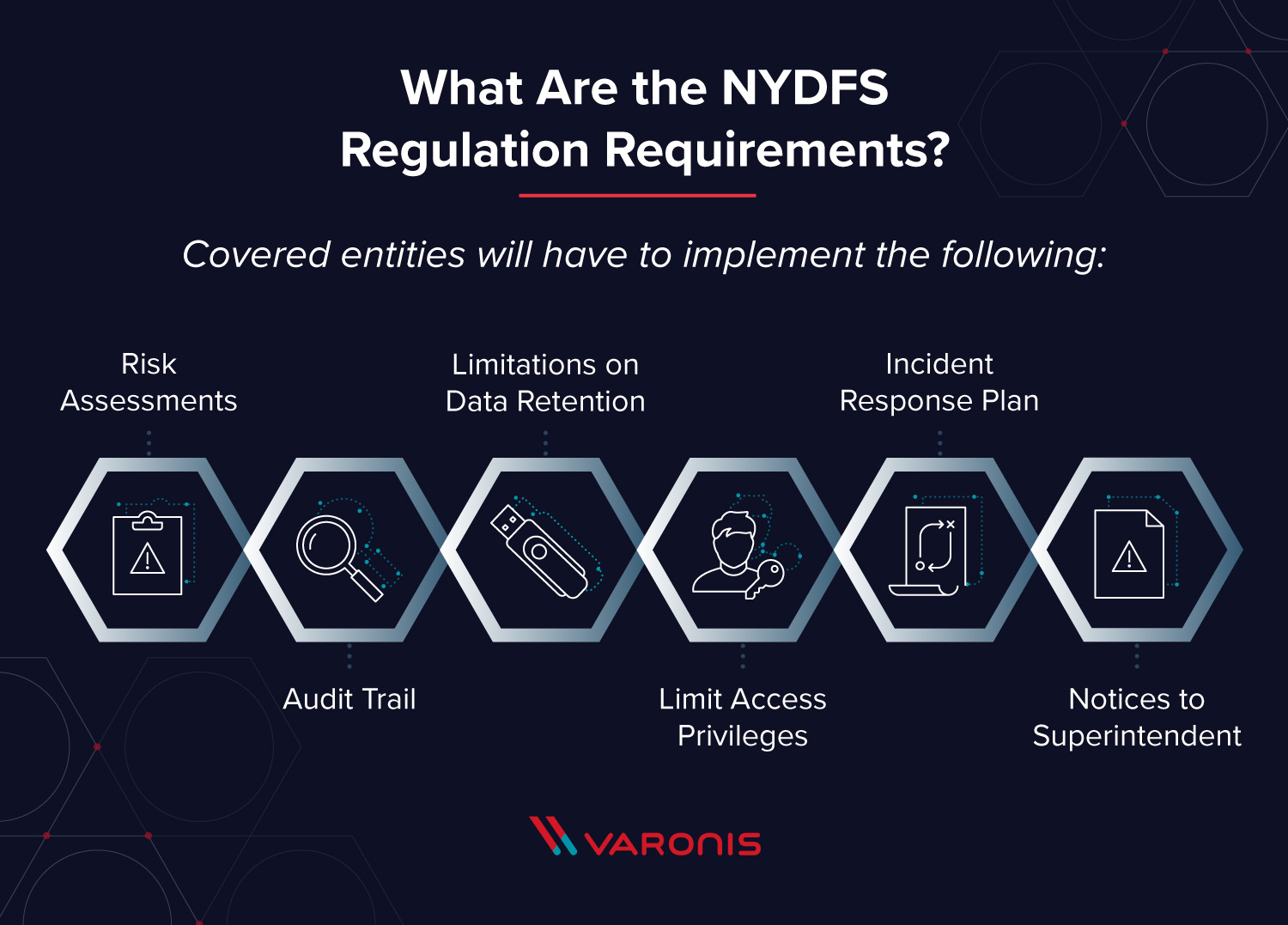
Covered entities will have to implement the following:
There are few important points to keep in mind about the NYDFS regulations:
| NYDFS Requirement | |
| Section 500.02 Cybersecurity Program. | Varonis detects insider threats and cyberattacks by analyzing data, account activity, and user behavior; prevents and limits disaster by locking down sensitive and stale data; and efficiently sustains a secure state with automation. |
| Section 500.06 Audit Trail. | Varonis gives you a single unified platform to manage risk and protect your most important assets, along with built-in reports and a detailed, searchable audit trail of data access. |
With a unified audit trail, admins or security analysts are only a few clicks away from knowing who’s been opening, creating, deleting, or modifying important files, sites, Azure Active Directory objects, emails, and more.
DataPrivilege gives business users the power to review and manage permissions, groups, and access certification, while automatically enforcing business rules.
The Automation Engine discovers undetected security gaps and automatically repairs them: fixing hidden security vulnerabilities like inconsistent ACLs and global access to sensitive data.
Quarantine sensitive and regulated content, discover data to collect for legal hold, identify data to archive and delete, and optimize your existing platforms.
Detect unusual file and email activity, suspicious user behavior, and trigger alerts cross-platform to protect your data before it’s too late. Automatic response triggers can stop ransomware in its tracks, and mitigate the impact of compromised accounts and potential data breaches.
Visualize security threats with an intuitive dashboard, investigate security incidents – even track alerts and assign them to team members for closure.
NYDFS dictates that risk assessments are not just a good idea, but (at least in New York State) are required for financial companies. Get started with a free risk assessment: we’ll identify PII, flag excessive permissions, and help you prioritize at-risk areas – and take the first steps towards meeting NYDFS compliance.
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.
Michael Buckbee Michael has worked as a sysadmin and software developer for Silicon Valley startups, the US Navy, and everything in between.